- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- Re: SSID with PEAP & MSCHAPv2 authentication and C...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
SSID with PEAP & MSCHAPv2 authentication and CWP, and bypass CWP if MAC known
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-02-2024 04:41 AM
I have an SSID that uses PEAP and MSCHAPv2 authentication with a CWP. The RADIUS Server is external and my WAPs are Extreme AP4000s. I'm using the Cloud IQ to configure and manage the WiFi and APs. This all works fine.
What I'm wanting to do now is to configure MAC authentication to be tried first with CWP bypass if successful. It the MAC auth fails I'm wanting the PEAP/MSCHAPv2 to be done with CWP.
I've not been able to get this setup. Can someone tell me if this is possible and if so how is it configured?
Thanks,
Paul
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-14-2024 09:50 PM
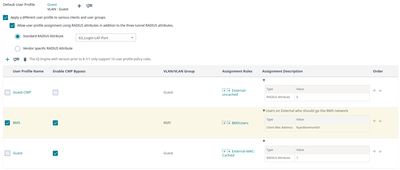
What you need to do is send a RADIUS attribute for known MAC addresses, and then match it in the user access settings at the bottom of the wireless network config. One thing to note is that even if it's going to be the same VLAN, you need two distinct user profiles, one for CWP and one without:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-08-2024 09:57 AM
Hi James, the RADIUS Server does do CoA but this is something that I'm not too clued up on. What I use is a Lab WAP and I make sure that this is cleared down of all associations and cache before I next try a test. So each test is done with a blank WAP. The only thing that I may change is whether the client MAC Address is in the RADIUS Servers database of endpoints or not.
I have seen another community query on MAC Bypass and fallback to CWP. This stated the WAP should have a change made via the command line. I don't know if I need to do something similar or if this applicable to older model WAPS. The article is: Solved: External CWP with mac-auth and CWP bypass. Users ... - Extreme Networks - 71431
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-11-2024 01:14 AM
CoA is change of authorisation, that allows sending a new profile to the AP after captive portal authentication succeeds. For your case, I thought it might be possible to send a CoA for MAC auth after joining with 802.1X auth. ISE does support CoA but I don't know if it would work in this scenario. A blank AP isn't an issue for CoA, it's for changing profiles (and other things) after a device has authenticated.
The article you linked is from 5 years ago and refers to a very old version of HiveOS (6.x vs 10.x these days). I don't think it's particularly relevant
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
01-14-2024 09:50 PM
What you need to do is send a RADIUS attribute for known MAC addresses, and then match it in the user access settings at the bottom of the wireless network config. One thing to note is that even if it's going to be the same VLAN, you need two distinct user profiles, one for CWP and one without:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-06-2024 09:52 AM
This is not the correct answer in my case. I don't know who marked it as correct but it wasn't me. It still isn't working as I want it to.
When I have the MAC Auth and SSID Auth configured I can see on the external RADIUS Server (Cisco ISE) that when a client connects it performs both the MAC Auth and then the SSID Auth. If one of these is unsuccessful the client isn't allowed to connect. So both Auths must pass. If there is a failure the client retries after about 10 seconds.
Upon successful authentication of both MAC and SSID the profile is applied according to the returned radius attribute. However as a value is returned for the succesful MAC Auth and then a different value is returned for the SSID Auth, the latter winds and this causes the CWP and AUP to be done.
I want the CWP and AUP not to be done if the MAC Auth is successful. How do I achieve this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-06-2024 09:58 PM
Hmm, I didn't notice you were doing 802.1X (what you call SSID) auth as well as MAC auth. It's not a common configuration, given that 802.1X includes the MAC address of the client, can you check that in the same rule as PEAP in ISE and return accordingly?