This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- Extreme Networks
- Community List
- Wireless
- ExtremeWireless (General)
- NAC authentication and mgmt authentication with th...
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
NAC authentication and mgmt authentication with the same radius servers
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-01-2019 06:26 AM
In my test environment I have a switch (X440G2 22.7.1.2) configured for NAC with two radius servers.
In the AAA configuration I see two netlogin radius entry’s and the radius mgmt.-access is disabled and the policy works fine.
As expansion on the configuration I want also that management requests are done by the radius servers.
So I configure the same radius server as for authentication .
Now I see in the AAA configuration that the netlogin rules are replaced by mgmt.-access rules and that the radius netlogin is disabled.
Cann’t I use the same radius servers for mgmt. as for authentication?
In the AAA configuration I see two netlogin radius entry’s and the radius mgmt.-access is disabled and the policy works fine.
As expansion on the configuration I want also that management requests are done by the radius servers.
So I configure the same radius server as for authentication .
Now I see in the AAA configuration that the netlogin rules are replaced by mgmt.-access rules and that the radius netlogin is disabled.
Cann’t I use the same radius servers for mgmt. as for authentication?
Johan Hendrik
System Architect
Audax
Solved! Go to Solution.
1 ACCEPTED SOLUTION
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-06-2019 05:56 AM
7 REPLIES 7
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-06-2019 09:02 AM
Ryan,
it works.
Thanks for your support.
it works.
Thanks for your support.
Johan Hendrik
System Architect
Audax
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-06-2019 05:56 AM
Ryan,
I will test it
I will test it
Johan Hendrik
System Architect
Audax
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-05-2019 03:55 PM
Hello,
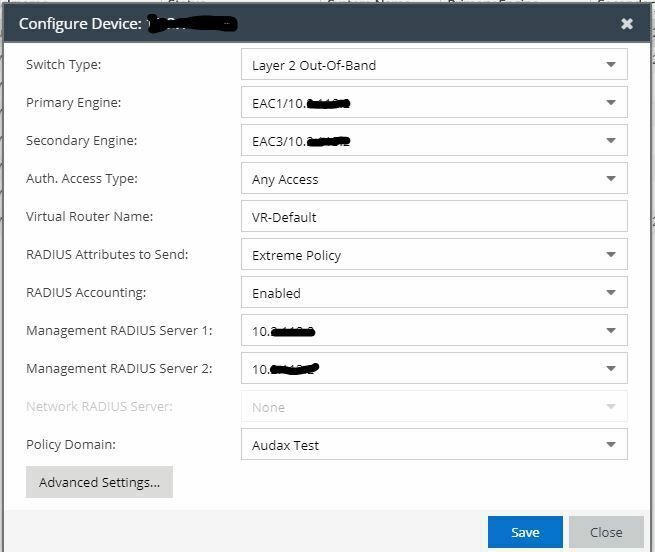
Remove the "Management RADIUS server" and "Management RADIUS server 2" servers. Set them to none.
If you identify Primary Engine and Secondary Engine as the NAC appliances you only need to set the "Auth Access Type" to any. This will identify them to be used for netlogin and mgmt access and configure the switch accordingly.
That should configure the AAA to use the NAC appliances for both netlogin and mgmt login.
Thanks
-Ryan
Remove the "Management RADIUS server" and "Management RADIUS server 2" servers. Set them to none.
If you identify Primary Engine and Secondary Engine as the NAC appliances you only need to set the "Auth Access Type" to any. This will identify them to be used for netlogin and mgmt access and configure the switch accordingly.
That should configure the AAA to use the NAC appliances for both netlogin and mgmt login.
Thanks
-Ryan
Options
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
08-05-2019 02:21 PM
I'm refering to th switch configuration of the AAA section.
At the moment I configure the management radius the config of the primairy and secondary engin are gone.
Config exaples:
Switch is configured for only primairy and secondary engins.
configure radius 1 server 1812 client-ip vr VR-Default
configure radius 1 shared-secret encrypted "#$QHoAV1JRHL25Psky9286ihA/eQb5twIipuhGzDsLDrL3fId9ua4zlQA6tElrf8XmjmCsk55g"
configure radius 2 server 1812 client-ip vr VR-Default
configure radius 2 shared-secret encrypted "#$3YuouBFWEkEJ3aeHDxVM+YcELVg0sPdr67z3lZouVh/r+QyCfaG/bfQ7GI1MPpu/X5ed7Xc1"
configure radius-accounting 1 server 10.2.112.2 1813 client-ip 10.2.112.209 vr VR-Default
configure radius-accounting 1 shared-secret encrypted "#$qdZB1R6z+Up25O4vjfhESlE3MvJhBdSaOdCuaG/stlu6uNlfXpNJbAdUMTFwdifnKnPlmCFc"
configure radius-accounting 1 timeout 10
configure radius-accounting 2 server 10.2.113.2 1813 client-ip 10.2.112.209 vr VR-Default
configure radius-accounting 2 shared-secret encrypted "#$6ygkfu3I9oANOxxLOXakeFXo1/6A38wnFhe1gWuENAqkCzjZI158UJ/UNs3XviNa0DnZ/Xrw"
configure radius-accounting 2 timeout 10
enable radius
enable radius mgmt-access
enable radius netlogin
Switch is configured for the both engins and both management radius:
configure radius mgmt-access 1 server 1812 client-ip vr VR-Default
configure radius 1 shared-secret encrypted "#$fipO29phKcl+o6SgtbPEZ6unyZrmd6sZ+nT58kRLJJFVq1lx0QXIXO5QyxHrm5y6rzWgp7H6"
configure radius mgmt-access 2 server 1812 client-ip vr VR-Default
configure radius 2 shared-secret encrypted "#$la/QbhlmQf2p7xkkNHgaE2pR9SWjFaQ7cGCbBbr3BueEieI5Iy65o7XwAqNXx2DLlECTwJBp"
enable radius
enable radius mgmt-access
enable radius netlogin
configure radius timeout 15
enable radius-accounting
enable radius-accounting mgmt-access
enable radius-accounting netlogin
At the moment I configure the management radius the config of the primairy and secondary engin are gone.
Config exaples:
Switch is configured for only primairy and secondary engins.
configure radius 1 server 1812 client-ip vr VR-Default
configure radius 1 shared-secret encrypted "#$QHoAV1JRHL25Psky9286ihA/eQb5twIipuhGzDsLDrL3fId9ua4zlQA6tElrf8XmjmCsk55g"
configure radius 2 server 1812 client-ip vr VR-Default
configure radius 2 shared-secret encrypted "#$3YuouBFWEkEJ3aeHDxVM+YcELVg0sPdr67z3lZouVh/r+QyCfaG/bfQ7GI1MPpu/X5ed7Xc1"
configure radius-accounting 1 server 10.2.112.2 1813 client-ip 10.2.112.209 vr VR-Default
configure radius-accounting 1 shared-secret encrypted "#$qdZB1R6z+Up25O4vjfhESlE3MvJhBdSaOdCuaG/stlu6uNlfXpNJbAdUMTFwdifnKnPlmCFc"
configure radius-accounting 1 timeout 10
configure radius-accounting 2 server 10.2.113.2 1813 client-ip 10.2.112.209 vr VR-Default
configure radius-accounting 2 shared-secret encrypted "#$6ygkfu3I9oANOxxLOXakeFXo1/6A38wnFhe1gWuENAqkCzjZI158UJ/UNs3XviNa0DnZ/Xrw"
configure radius-accounting 2 timeout 10
enable radius
enable radius mgmt-access
enable radius netlogin
Switch is configured for the both engins and both management radius:
configure radius mgmt-access 1 server 1812 client-ip vr VR-Default
configure radius 1 shared-secret encrypted "#$fipO29phKcl+o6SgtbPEZ6unyZrmd6sZ+nT58kRLJJFVq1lx0QXIXO5QyxHrm5y6rzWgp7H6"
configure radius mgmt-access 2 server 1812 client-ip vr VR-Default
configure radius 2 shared-secret encrypted "#$la/QbhlmQf2p7xkkNHgaE2pR9SWjFaQ7cGCbBbr3BueEieI5Iy65o7XwAqNXx2DLlECTwJBp"
enable radius
enable radius mgmt-access
enable radius netlogin
configure radius timeout 15
enable radius-accounting
enable radius-accounting mgmt-access
enable radius-accounting netlogin
Johan Hendrik
System Architect
Audax