- Extreme Networks
- Community List
- Network Management & Authentication
- ExtremeControl
- Re: Extreme Control as External RADIUS in Cloud IQ
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Extreme Control as External RADIUS in Cloud IQ
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-22-2022 04:21 AM
I understand that it is possible to create a network policy in Cloud IQ for Wireless which can use External RADIUS server for authentication (Extreme A3, NPS, Extreme Control). Do the APs (AP3705C) which are onboarded in the cloud also need to be added under Access-Control>Switches? If so what RADIUS Attributes should they use?
Thanks,
Rob
Solved! Go to Solution.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
03-01-2022 02:05 PM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-24-2022 12:51 PM
###################################################################
# Update the Bearer Token, client secret, client-id,
# redirect-uri, and ownerid in the curl_cmd variable to
# match your developer credentials, bearer token from
# XIQ, and VIQ ID.
# Developer credentials: https://developer.aerohive.com/
# Bearer Token: XIQ Interface/Global Settings/ API Token Management
# VIQ ID: From the XIQ interface "About" menu option
###################################################################
curl_cmd = 'curl -s -k --header "Authorization: Bearer xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"'
curl_cmd = curl_cmd + ' --header "X-AH-API-CLIENT-SECRET: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx"'
curl_cmd = curl_cmd + ' --header "X-AH-API-CLIENT-ID: xxxxxxxx"'
curl_cmd = curl_cmd + ' --header "X-AH-API-CLIENT-REDIRECT-URI: https://x.x.x.x"'
curl_cmd = curl_cmd + ' https://va2.extremecloudiq.com/xapi/v1/monitor/devices{?ownerId=xxxxxx}'
I've found the ownerId and REDIRECT-URI address (my XIQ-SE) but struggling to find the CLIENT-ID and complete the first three lines?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-24-2022 11:18 AM
One thing that failed in my setup was the Workflow to Import the XIQ APs. When I ran it it said it succeeded very quickly as if it did not run through all of the tasks. No APs were added to XIQ-SE and no APs were added to Access-Control.
The output for the workflow showed an error:
Script Name: Process New XIQ Devices_Extract_All_Devices_from_XIQ
Date and Time: 2022-02-24T16:19:51.443
XIQ-SE User: netsight
XIQ-SE User Domain:
IP:
code: GatewayErrorCode.CLIENT_VERIFICATION_FAILED
message: Client Credential verification failed.
rawMessage: XCKCKzThhF
status: 401
I imported the workflow and appeared to succeed but nothing happened. Any ideas?
Thanks
Rob
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-23-2022 08:11 AM
Hello Robert,
That is a great document that was developed by our TME team. I use it myself all the time.
To answer your questions for future use:
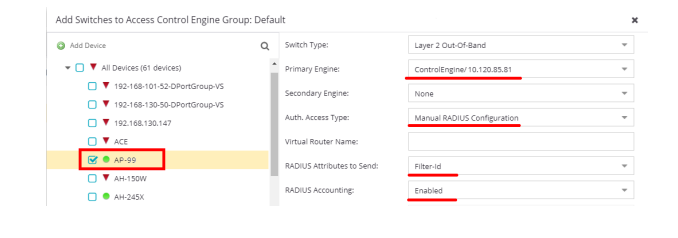
The AP's needed to be added into the Control --> Switches tab.
Extreme Control/A3 both can have local users or integration with AD.
Thanks
-Ryan
Adding APs into the Control switches tab will add them to a clients.conf file that will make them authorized for RADIUS communication. Without them in the clients.conf file NAC will not respond to RADIUS requests from their IP address.
We use filter-ID for role assignment with XIQ.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-23-2022 08:11 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Get Direct Link
- Report Inappropriate Content
02-22-2022 01:01 PM
https://documentation.extremenetworks.com/ExtremeCloudIQ/HowTo/ExtremeControl_for_XIQ-SE_and_XIQ_APs_How-to_Guide.pdf
These are the sort of guides we all find useful and give great guidance with examples which are easy to follow and apply. It would be difficult to know what to do otherwise.