Resolved! XIQ-SE - deploy platform installation
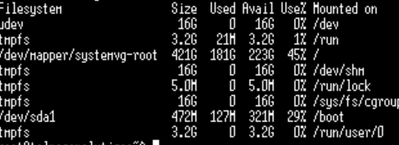
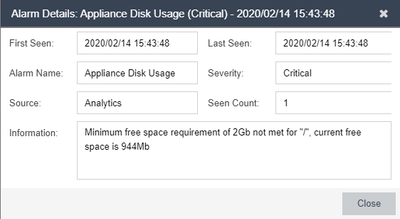
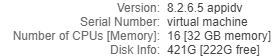
Hi Team!!!In my case, historical deploys were made over VMWARE hypervisor, but now we have a problem with them.WMARE will increase prices a lot and a lot of customer are asking for alternate hypervisors, I see that HyperV is supported but we are look...